Description
…
You have a folder containing some windows artifacts:
- Users Dir that has one user folder (person).
$ExtendDir that has only$UsnJrnlfile ($J).- system hives inside windows/System32/config
Let’s start with the user folder, you can see multiple random files in every folder, maybe one of the files was stolen from here, but which one? and how was it stolen?
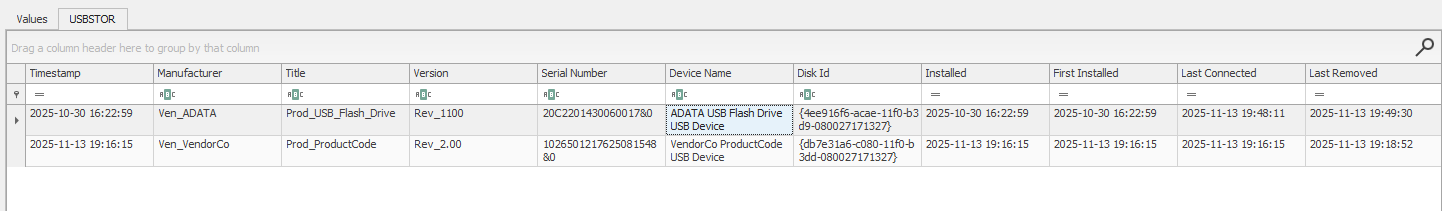
Usually in these scenario you’ll find some exfil methods, but there isn’t any suspicious executables or scripts in the user folder, investigating the SYSTEM hive can lead to identifying two usb entries, maybe the attacker used a usb to exfil the file, loading the SYSTEM hive into RegistryExplorer we can see the two usbs at HKLM\ControlSet001\Enum\USBSTOR:
- ADATA USB Flash last connected at
2025-11-13 19:48:11 - VendorCo USB last connected at
2025-11-13 19:16:15
Now to find out exactly what files got stolen you need correlate the timeline with the $J file from the $Extend dir,parse the file with MFTECmd.exe and open the csv with timeline explorer.
Filter for DeleteFile and timestamp should after VendorCo last connection 2025-11-13 19:16:15 and before last Removed 2025-11-13 19:18:52

doing the same with the other usb:
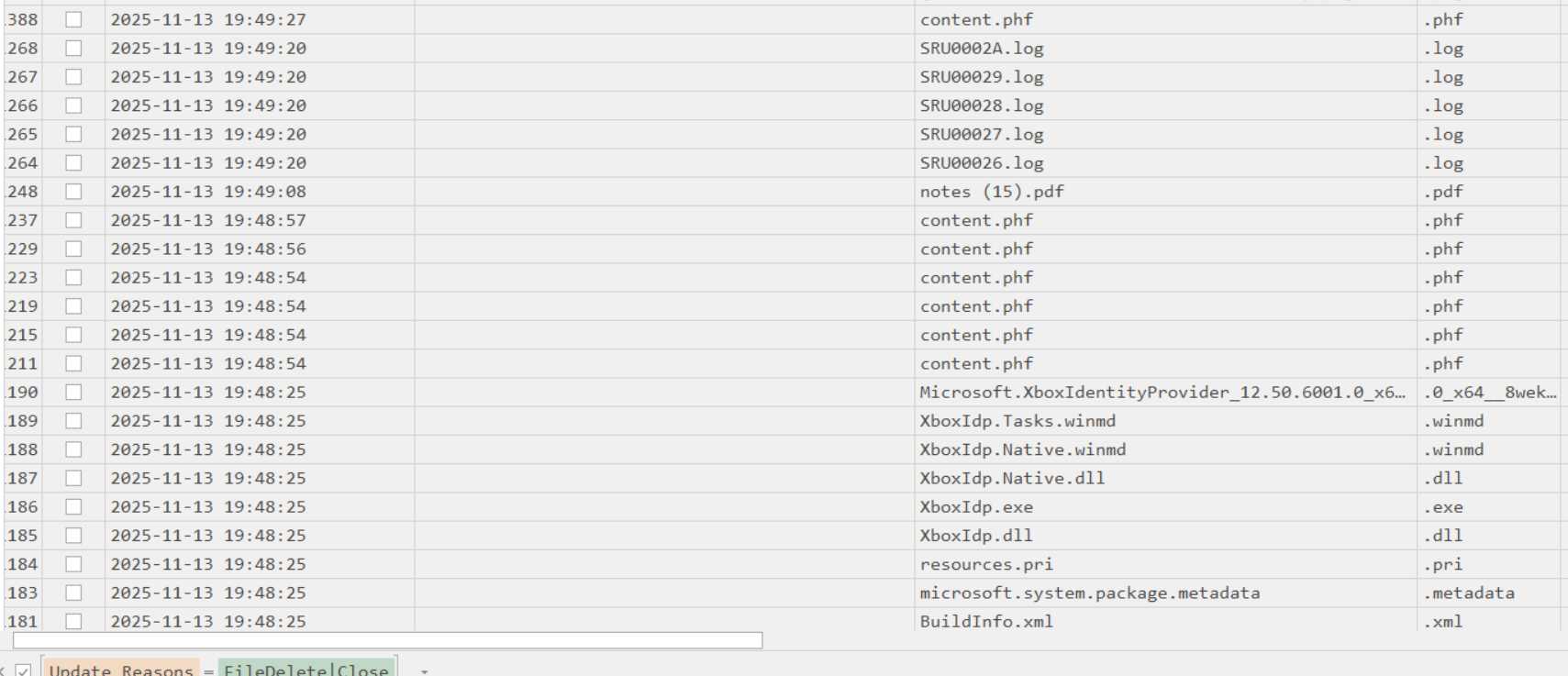
one file stands out here is notes (15).pdf and it’s the correct one.
Osint Part: Identifying the attacker
now that we have the stolen file, we need something to identify the attacker, let’s investigate the AppData Dir:
ls AppData/Roaming/$I30 Adobe discord Microsoft Mozilla ThunderbirdThunderbird is a mail client from mozilla, this should be your first target since it’s easy to investigate.
➜ Profiles ls8k8hw17u.default-release xulck67c.default➜ Profilesyou can open that folder using this tool to view emails from thunderbird client:

from this suspicious email we can see that the attacker uses the username mhunter0x3 and the email mhunter3756@gmail.com.
Searching for that username on X, we can find this account which has reposted cascroot’s tweet about an htb ctf.
searching for that same username on reddit, you’ll get this profile, you gotta inspect display names to find the exact profile. you’ll the find the attacker replied to a post on r/algeria under the flare jijel
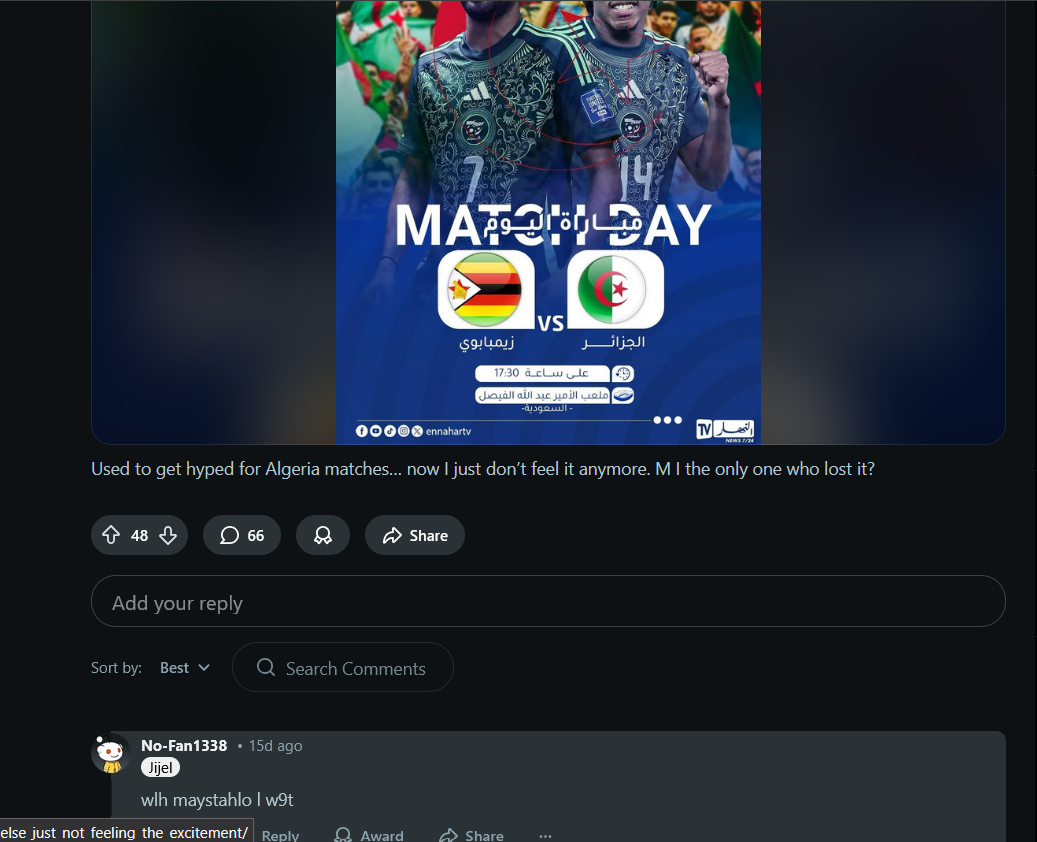
now we know that the attacker is from jijel, algeria, and he’s most likely a member in the cascroot team, going to cascroot’s linkedIn page, under the people section, we can identify the member from jijel as Abderrahman Daidou.
Flag:
nexus{Abderrahman_Daidou_notes_(15).pdf}
